Cryptography is the backbone of distributed ledger technologies like blockchain and other consensus-oriented distributed networks. If you are interested in building decentralized applications, for example, it’s essential to understand wallet generation and transaction signing processes. Both of these rely heavily on underlying cryptographic protocols for network security. With the advancements in cryptocurrency and defi, the question “What is cryptography?” leads directly to the cyber world.
Cryptography is a critical component of cyber security. With cybercrime on the rise and cyber attacks costing businesses an average of 2.3 Million dollars per malware attack, it is increasingly important to have your cybersecurity up to par. With the proper use of cryptography, you could save your business significantly, by ensuring the confidentiality of digitized sensitive information.
Modern cryptographic systems are mathematically robust. They help to secure sensitive information like your bank account numbers and Social Security number. While the mathematics may be complex, the concepts can be grasped without a complete understanding of encryption algorithms.
One of the key components of cryptography is ciphers. Ciphers are algorithms used to conceal (encrypt) and decrypt information. Encrypted information is called ciphertext, while decrypted information is called plaintext. There are two types of ciphers: symmetric ciphers and asymmetric ciphers. Let’s look at the difference and some examples.
What are the three types of Cryptography?
Symmetric key encryption
Symmetric key cryptography, also known as single key cryptography, means the same key is used both to encrypt and decrypt information. One of the earliest examples of symmetric encryption is known as Caesar’s Cipher or shift cipher.
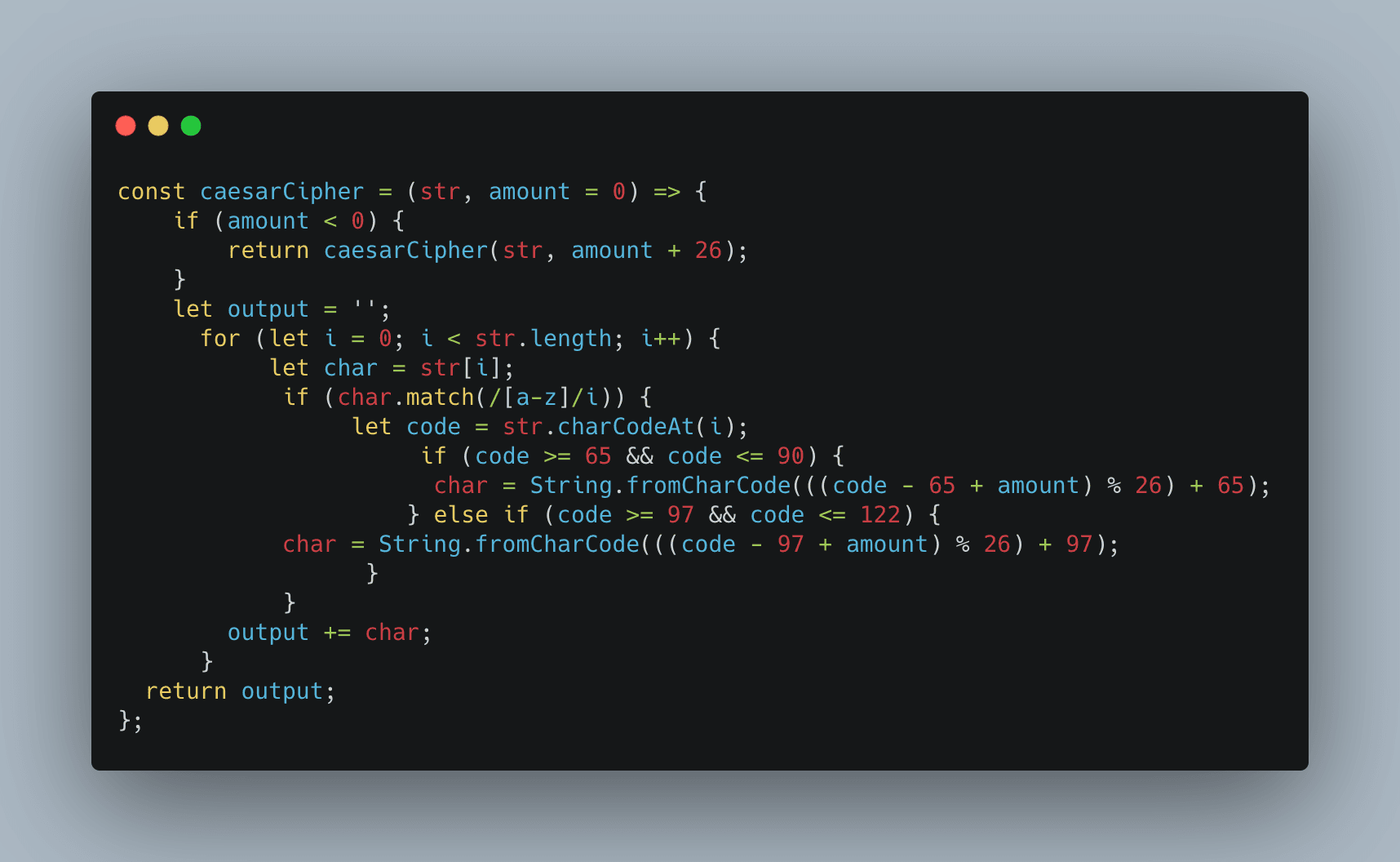
The Caesar cipher works by mapping the plaintext letter to a character of a predetermined distance (the key) adjacent in the alphabet. For example, if the key is a right rotation by three, then “A” gets mapped to ”D”. The whole keymap has been constructed below for your convenience. The plain-text, “CIRCERO,” would be enciphered as “FLUFHUR.”
Notice that the wraparound of the alphabet is modeled by modulus arithmetic. We can mathematically represent an encryption [En=(x + n)mod 26] and a corresponding decryption function [Dn= (x – n)mod 26]. Here is an excellent code repository of the implementation of this algorithm in several different languages. Below is an example constructed in JavaScript.
|
Plaintext |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|
Ciphertext |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
For some time, transposition ciphers like the shift cipher provided adequate protection of sensitive information. However, enumerating over 26 possible keys isn’t hard, and the cipher is easily broken using a one key cryptographic system.
Asymmetric key encryption
Modern ciphers, which make distributed ledgers like blockchain possible, are known as asymmetric ciphers. Asymmetric ciphers use one key, known as the public key, to encrypt information and a second key to decrypt information. These two keys are known as the private and public key cryptography pair. In symmetric cryptography, the same secret key used to encrypt information also decrypts information.
If you’ve poked around the distributed ledger space, chances are you’ve generated a wallet. A wallet consists of a Private Key, to keep secret, and a Public Key, which acts as your wallet’s address. We will go over how crypto wallets use asymmetric cryptography.
Before asymmetric cryptography, people had trouble carrying out key exchanges over long distances. To share private information over a secure communication channel, you and the receiving party need to share a key. You can see this chicken or the egg problem forming. How do you securely share the key? Asymmetric ciphers and secret key cryptography addressed this issue.
Asymmetric cryptography works as follows. Say Alice and Bob want to send a secret message without an eavesdropper, Eve, able to read the message. Alice and Bob each have a public key, viewable by anyone. They each have a private key (only known by the owner of the corresponding private key). Alice will encrypt data with Bob’s Public Key so that only Bob’s Private Key can decrypt her message. Alice sends the message to Bob. Even if Eve can intercept the message, she cannot read its contents without Bob’s Private Key. Bob can then decrypt the message with his private key and read the secret message from Alice.
Hash functions
Cryptographic hash functions are a contemporary form of cryptography that doesn’t use any key at all. Instead, the cipher uses complex mathematical concepts to convert the input into an output known as the “hash value.” Hash values are always a fixed length of numbers and letters, unique to the input and the hash function. Hash values are also near impossible to reverse-engineer to plaintext because there’s no apparent predictability to the hash function.
Say we run the plaintext words “Hedera Hashgraph” through the hashing algorithm SHA-256. We’ll end up with a string of 64 numbers and letters. Then let’s change the plaintext to “Hedera hashgraph.” We’ll have a totally different composition of 64 numbers and letters, with no relevance at all to the first set. This is what’s known as the “avalanche effect,” where the smallest tweak in data radically changes the result.
Hash functions make storing data on blockchains reliable, secure, and immutable. These hashes act as links connecting blocks together on the chain. If there’s any change in block data, the avalanche effect invalidates the data in the encryption process. This causes a break in the blockchain.
What is cryptography used for?
All methods of cryptography function to ensure secure communications, visible only to the sender and receiver. But there are four tenets to ensure that ciphers and software for data protection meet the data encryption standard.
-
Keep data confidential. Data privacy is a baseline for encryption. The transmitted data or encrypted message should be seen and understood by only the intended recipient.
-
Preserve integrity of data. No one can change information while the data is in transit or while it’s being stored, without the change being detected.
-
Message authentication. Both the sender and receiver can validate each other’s identity and confirm the origin or destination of the information.
-
Non-repudiation. A bit like digital signatures, creators or senders of data can’t later deny their creation or transmission of data.
From digital signing, key generation, protecting web browsing, or verifying credit and debit card transactions, cryptography is everywhere online. Now we’re going to look at a very specific application of encryption and cipher technology.
Ciphers used in blockchain wallets
So how do crypto wallets leverage this technology? When you are authorizing transactions, you prove that you are the owner of the private key corresponding to the wallet. This is done using a Digital Signature Algorithm, an example of asymmetric key cryptography.
A user authorizes a transaction by providing proof that the user is the owner of the private key corresponding to the public key’s funds. Because of the mathematical relationship between the public and private keys, a user can sign a transaction with their private key creating a digital signature. A digital signature reveals no information about the private key but can be verified with the corresponding public key. Thus proof can be constructed.
The currently best performing asymmetric encryption algorithm is the Elliptic Curve. Elliptic Curve provides fast, secure encryption with a smaller key than RSA.
Hedera uses Elliptic Curve operations and native hashing through programming languages like Vyper and Solidity. Since 2018, Hedera Hashgraph has met the Asynchronous Byzantine Fault Tolerance (ABFT), the gold standard for security in distributed systems.
For readers interested in the mathematics of RSA or the Elliptic Curve, the following resources are excellent learning tools.
• Elliptic Curve
• RSA (Rivest, Shamir, Adleman)
• DSA (Digital Signature Algorithm)
• ECDSA (Elliptic Curve Digital Signing Algorithm)
Resources on the implementation and available cryptography libraries are presented below. These are all open source and generally respected and implemented for various purposes.
• Crypto-js Is a great JavaScript library to explore additional ciphers
• elliptic is a JavaScript library for elliptic curve encryption including digital signature algorithms.
• Cryptography is an expansive python library with access to digital signature algorithms and most commonly used ciphers.
• OppenSSL is commonly used by system administrators to generate TSL certificates, and perform cryptographic functions.
• Botan is a crypto library for C++.
• Bouncy Castle has a Java and C# library and is a provider for the Java Cryptography Extension (JCE).

