Blockchain & distributed ledger origins
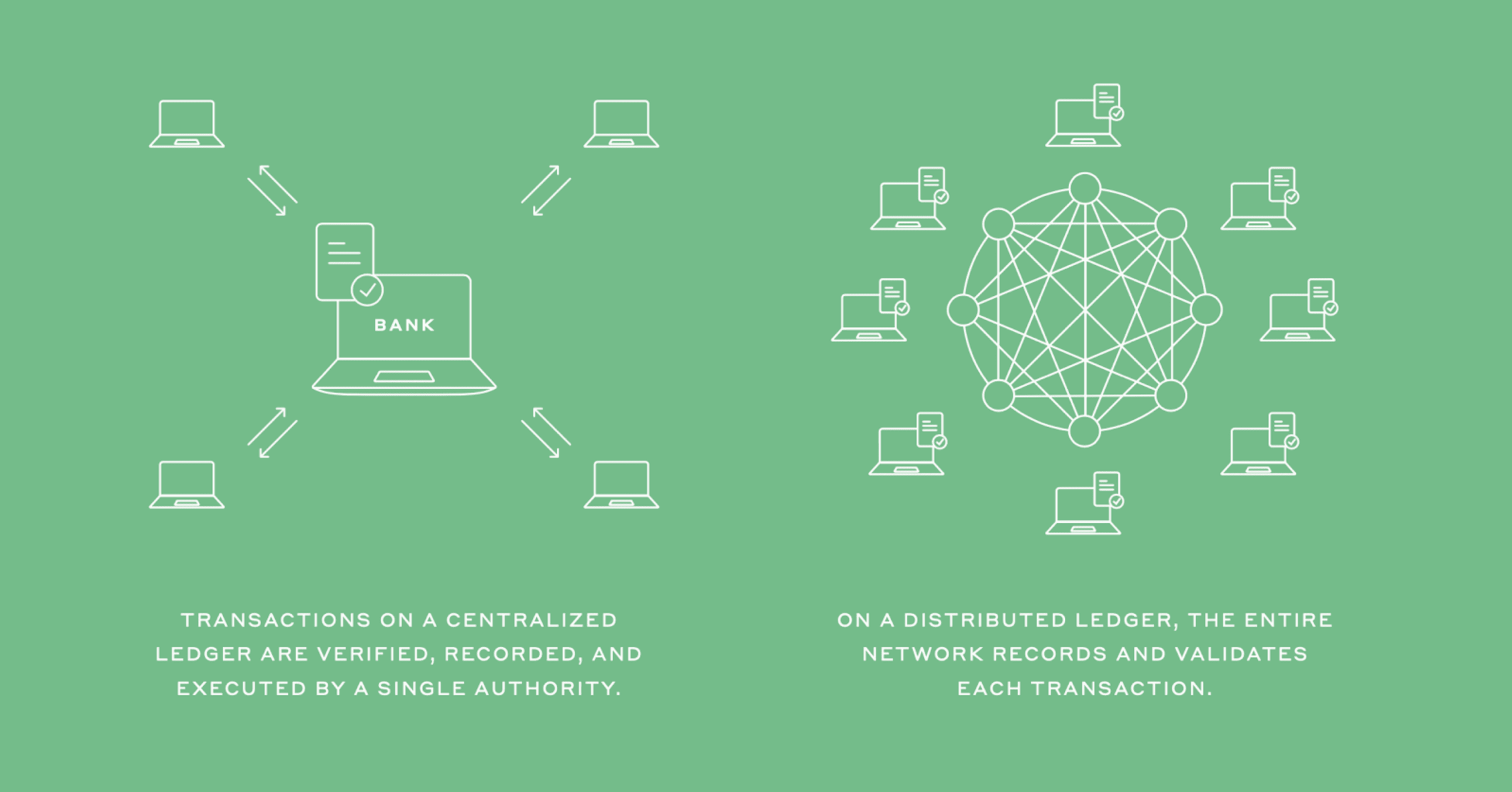
In a traditional marketplace, middlemen oversee the exchange of assets. When you receive your paycheck, for example, a bank controls the transaction. The bank validates the check, verifies that the employer holds the required funds in their account, and records the exchange. This record, or ledger, documents the transaction and the resulting change in wealth; you can look at your bank statement and see that you’re a little bit richer. For most transactions, a central entity like a bank has sole power over this ledger.
While giving control of our transactions to a central power requires a great deal of trust, it has historically been the best method for ensuring the security of the ledger. Imagine, for instance, that your employer owned the ledger instead of the bank. Your employer could falsely claim that they paid you and manipulate the records to back up their lie. Because of this security risk, neither participant in the exchange should be given sole control of the ledger. For most of history, the best way to avoid this kind of fraud was to entrust an unbiased intermediary with the ledger and hope that this middleman would faithfully maintain the ledger. In other words, traditionally, two parties who agreed upon a transaction relied on a third-party institution to carry out and record the exchange.
However, central ledgers are no longer the only viable option for exchanging our assets. Now, due to the advent of distributed ledger technologies, we can safely get our paychecks without needing to trust a bank.
Blockchains & distributed ledgers explained
Distributed ledger technologies, like blockchain, are peer-to-peer networks that enable multiple members to maintain their own identical copy of a shared ledger. Rather than requiring a central authority to update and communicate records to all participants, DLTs allow their members to securely verify, execute, and record their own transactions without relying on a middleman.
While there are a wide variety of DLTs on the market, they are all comprised of the same building blocks: a public or private / permissioned / permissionless distributed ledger, a consensus algorithm (to ensure all copies of the ledger are identical), and a framework for incentivizing and rewarding network participation.
Public vs. private and permissioned vs. permissionless
Distributed ledgers are categorized as “private” or “public” and “permissioned” or “permissionless” — they can be any combination of any of the two. To achieve full decentralization, Hedera believes distributed ledgers must be public permissionless networks.

Private / Permissioned: This type of network offers no decentralization. The applications and the network nodes running those application must both be invited to join the network and meet certain criteria or provide a form of identification. Any party can also be removed without warning at any time.
Private / Permissionless: Requires that applications deployed in production be invited to join the network and can be removed without warning at any time. The nodes which constitute the network and run said applications can freely and anonymously join and contribute, typically in exchange for a network’s native cryptocurrency.
Public / Permissioned: Allows applications to be deployed in production or removed, without having to notify anyone, reveal their identity, or meet any application criteria requirements. The nodes which constitute the network and run said applications must be invited to join the network.
Public / Permissionless: This type of network is the most decentralized. Applications can be deployed in production or removed, without having to notify anyone, reveal their identity, or meet any application criteria requirements. Additionally, the nodes which constitute the network can freely and anonymously join and contribute, typically in exchange for a network’s native cryptocurrency.
Reaching consensus
Although every node on a permissioned or permissionless distributed ledger maintains and updates their own copy of the ledger, it is imperative that each of these ledgers remains identical. Imagine, for instance, that your copy of the ledger reveals that you have $100 in your account, while the cashier’s ledger holds that you have $1. This discrepancy would make it very difficult, if not impossible, to buy a candy bar. Without identical ledgers, participants in the network could not make transactions.
In order to keep the distributed ledger consistent, DLTs must have a consensus algorithm, or a method of ensuring that all copies of the ledger agree. A consensus algorithm is a method of synchronizing the data across a distributed system. In the case of a DLT, the consensus algorithm ensures that all copies of the ledger are identical.
There are many different consensus algorithms on the market, each with different advantages. Perhaps the most intuitive algorithm is a simple vote. According to this algorithm, each node independently calculates how they think they should update their ledger based on the information available to them. Then, each node sends this information to every other node. At this point, every node in the network has access to their decision and every other node’s decision. The nodes then calculate the majority or plurality vote, and they all update their ledgers according to this democratic consensus.
Although the simple vote is effective and intuitive, it is not efficient at scale. Because every node must send their vote to every other node, the bandwidth and processing power required to come to consensus grows exponentially with the size of the network. In other words, every additional node dramatically decreases the efficiency of the network. Because DLTs become more secure and transparent when more nodes are added to the network, many other consensus algorithms have been developed to better suit the need for large, efficient, and reliable peer-to-peer networks.
If you are curious about other consensus algorithms, you can learn about them by visiting the following pages within the learning center: voting-based consensus, economy-based consensus, and more coming soon.
Cryptocurrency and compensating network participants
To carry out their consensus algorithms, DLTs require a significant amount of processing power per transaction. Just as DLTs distribute the responsibility of maintaining the ledger to each participant, so do they divide this computational burden. Every node must donate computing power to run the consensus algorithm and process transactions. Of course, computing power is not free.
To compensate participants for their work, and incentivize further participation, DLTs typically reward active membership with cryptocurrency. Cryptocurrency is a virtual, encrypted token which can be exchanged using across a decentralized network. These coins can be exchanged, purchased, or earned by participating in the network.
While cryptocurrencies have no inherent value (much like fiat currency), they may be valuable to participants in a network because they are necessary for performing actions quickly, securely, and cost effectively across the decentralized network. Their usefulness as currency generates a demand for these coins. Therefore, participants have an incentive to contribute computational resources to the network. Not only is their work rewarded in cryptocurrency, the value of that currency may rise as the network grows and more build useful applications on the distributed ledger platform.
Why are distributed ledger technologies useful?
Distributed ledger technologies allow businesses and individuals alike to quickly carry out secure transactions without needing to rely on a middleman. By avoiding intermediaries, distributing control of the ledger, and providing a tamper-apparent network, DLTs present a more cost-efficient, accessible, and reliable transaction platform than centralized ledger systems.

Remove the middleman
Because central ledgers rely on intermediaries, they are burdened by the costs and inefficiencies of the middleman. DLTs do away with these limitations by avoiding middlemen and intermediaries altogether. Without a central agent, there is no need to pay a central agent. And, without the need for clunky bureaucracy, you can exchange assets directly and immediately. You no longer have to limit the speed of your transaction to the efficiency of expensive bankers, lawyers, or politicians.
Moreover, you no longer have to trust bankers, lawyers, or politicians with the ledger and your assets. DLTs are trustless systems, meaning that no participant needs to trust any other participant to guarantee a valid ledger.
Accessibility
While centralized systems monopolize control and limit access to their ledger, DLTs provide a much more accessible service. DLTs allow businesses and individuals to carry out transactions freely, without relying or trusting any other individual. Public DLTs take this further by issuing no restrictions on transactions or participation; no one can be denied from the platform, and no transaction will be treated with priority over another.
Tamper-apparent
Traditional ledgers may provide fast and simple record-keeping, but they are vulnerable to corruption and hacking. Because only one central entity controls the ledger, a corrupt central agent can tamper with the records without the consent or knowledge of the affected members. Moreover, because there is only one copy of the ledger, hackers have a clear, single target for their attacks. Without visibility into whether tampering has occurred, we must simply trust that the central third-party is neither corrupt nor compromised when we use a centralized ledger.
Distributed ledgers, however, are inherently resistant to tampering. While a malicious agent could compromise a central system by altering the single ledger, they would need to alter at least a plurality of ledgers to have an impact on a distributed system.
Though DLTs are not tamper-proof, they are tamper-apparent. That is, if tampering does occur, the network’s transparency ensures that all members of the network will be aware of the change. Though a participant of a DLT cannot be completely certain that the ledger will remain unaltered, they can rest assured that they will know if tampering does occur.
Hedera Hashgraph has achieved the gold standard of security in distributed ledger consensus mechanisms, which is asynchronous Byzantine fault tolerance (aBFT) and is the only distributed ledger to-date which has formally proven this quality. Hedera guarantees consensus, in real time, and is resistant to Distributed Denial of Service (DDoS) attacks, an area of vulnerability for some public ledger platforms.
Immutability and controlled mutability
Some distributed ledgers take security beyond tamper-apparent by establishing immutability, preventing any and all participants from changing established records for any reason. Members of these immutable DLTs can only view the ledger and carry out new transactions. Even if all participants in the network wished to change the ledger, there would be no pathway within the system’s architecture for that change to occur. Therefore, participants of an immutable distributed ledger can be certain that their ledger is not only tamper-apparent, but tamper-proof. A distributed ledger technology is immutable if it does not provide any participant or group of participants the ability to alter or delete established records.
Of course, immutability does come with downsides. In some cases, changing past records could be beneficial. For instance, if a bug in the DLT’s code causes a transaction to be misrepresented in the ledger, immutability would prevent anyone from fixing that problem. The invalid transaction would forever be part of the official ledger. Additionally, as laws change to catch up with technology, new government regulations may necessitate a change in record-keeping practices. Immutable systems would not be able to adapt to these changing legal conditions, and would therefore risk violating government standards.
Recognizing the downsides of both mutability and immutability, some DLTs opt for controlled mutability. DLTs with controlled mutability allow records to be changed, but place heavy restrictions upon that pathway.
Controlled mutability is the best of both worlds: no malicious participant or group of participants can alter the records without everyone knowing (tamper-apparent), but the DLT can adapt to bugs and changing regulations. Hedera Hashgraph is one example of a DLT with controlled mutability. Hedera Hashgraph will establish the Hedera Council, a diverse group of businesses across nearly every industry. The council will have the ability, through unanimous vote, to remove illegal or malicious content to abide by local and global regulations. Because the council will be completely transparent and bound by term limits, participants will observe and hold the council accountable for any changes that they may make to the ledger. By having the Hedera Council, Hedera Hashgraph provides a controlled mutability that retains security while allowing the DLT to adapt to changing government standards. To learn more about the Hedera Governing Council, visit: Hedera.com/council

